If you receive a message you are unsure about, ASK US! – Forward the message to phishing@marshall.edu. If you would like a reply, please be sure to ask a specific question when you forward a suspicious message. We receive many phishing reports per day and do not reply to all of them, but are happy to answer any questions you have!
- Change the password of the compromised account to something entirely different. NEVER use your old password again.
- If you have used the compromised password or a similar password on other sites, change each of them to something unique.
- Turn on multifactor authentication where possible.
- Consider using a password manager. (See Using a Password Manager Securely below.)
- Learn how to spot phishing messages and use caution before opening an attachment, clicking a link, or replying to an email in the future. (See How to Spot a Phishing Message below.)
- NEVER use previously compromised passwords on any account.
- Do NOT use a common password for multiple accounts.
- Do NOT use a common password theme with different variations for each account.
- Create complex passwords by using passphrases and multiple character types. For more on how to create complex passwords, visit 10 Rules for Creating Hacker-Resistant Passwords or watch this video on Lynda.com: Creating Memorable Complex Passwords.
- Check your email addresses on HaveIBeenPwned.com to determine if they have been on breach lists in the past.
- Turn on multifactor authentication where available, especially for financial accounts or accounts that have personal information associated with them.
- Change passwords periodically. Set a reminder on your calendar for once per year to change all account passwords, especially for financial accounts or ones that contain personal information or credit card data. If you do not use multi-factor authentication on those accounts, you might consider changing the passwords more frequently.
- Consider using a password manager that stores all of your passwords in a “vault” so you can have different passwords for every account without having to remember them. (See Using a Password Manager Securely below.)
Password managers are a great way to store credentials. To find out more about how password managers work watch this video on LinkedIn Learning.
It is important that you keep the password manager itself secure, or else a bad actor can obtain all of your stored passwords. Below are some best practices when using a password manager:
- Use a strong, long password for the password manager that you will remember. It should be unique and not used on any other account.
- Do not store credentials in the vault to the email account that was used to sign up for the password manager.
- You will need to remember two passwords: One for the password manager, and one for the email account you use when you register for the password manager. This email account password should not be stored in your vault. In the event that your password manager is compromised, your backup email account will still be available and uncompromised so you can change the password to the password manager.
- Use multifactor authentication for the password manager! (VERY IMPORTANT!)
- For accounts stored in the password manager, you can use long passwords with random letters+numbers+symbols since you will not need to remember them.
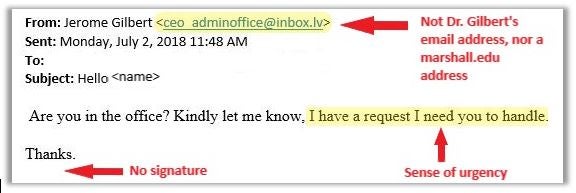
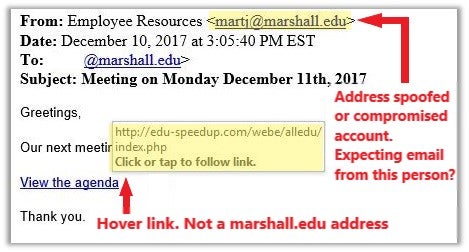
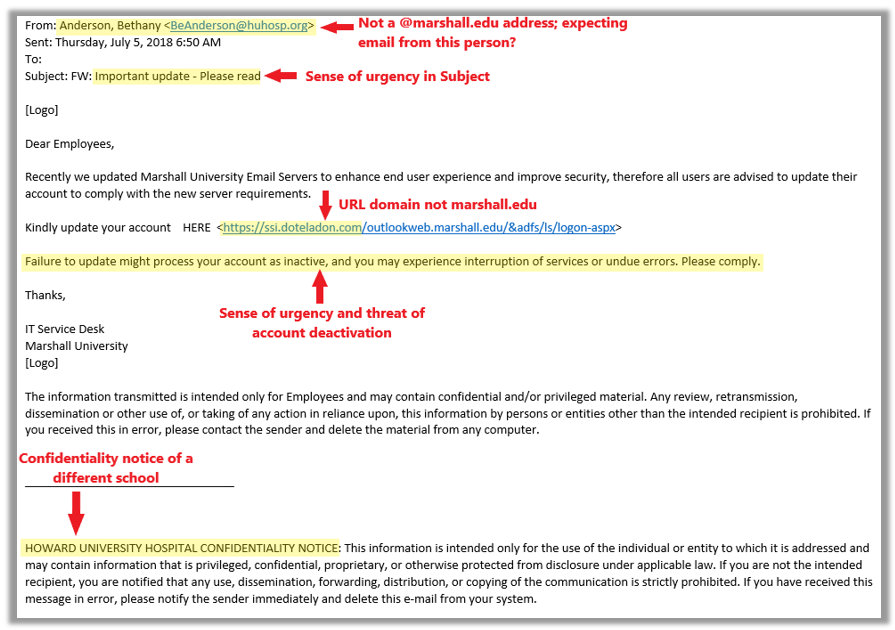
- Are you expecting this message? One of the best ways to spot a fraudulent message is to ask yourself if you were expecting it, even when you know the sender.
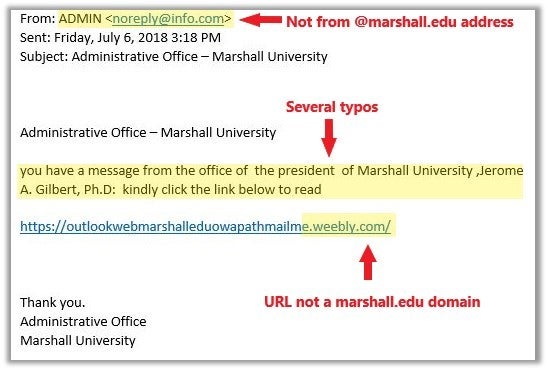
- Do you know the sender? Verify the email address, not just the display name. For example:
- Gilbert, Jerome <imthepresident@gmail.com>
- Microsoft Office365 <microsoft@homestarinc.com>
- Is the message written with a sense of urgency? For example:
- “Your account will be deactivated if you don’t act soon!”
- “A server has been updated and your account information needs verified.”
- “Important message!” (Especially when from an important person, such as president of the university.)
- “Important document to view!”
- Does the message have typos or other anomalies?
- Hover your mouse over links (without clicking) to reveal the URL…
- Is the URL what you would expect?
- Is the URL a shortened link, such as bit.ly, tinyurl.com, or goo.gl?
- Is the URL the legitimate website of the organization sending the message? (For example, if a message is claiming to come from an office of Marshall University, does the URL you are being asked to click begin with https://www.marshall.edu?)
- When in doubt, ASK US! – Forward the message to phishing@marshall.edu. If you would like a reply, please be sure to ask a specific question when you forward a suspicious message. We receive many phishing reports per day and do not reply to all of them, but are happy to answer any questions you have!
Below are some examples of phishing scams with clues that indicate this might not be a legitimate message: